- Aerodrome alerts users after attackers hijack its primary domains on the Base network.
- DNS breach triggered malicious approvals aimed at draining NFTs, ETH, USDC, and WETH.
- Over $1M was drained within an hour as users shared recordings of the phishing sequence.
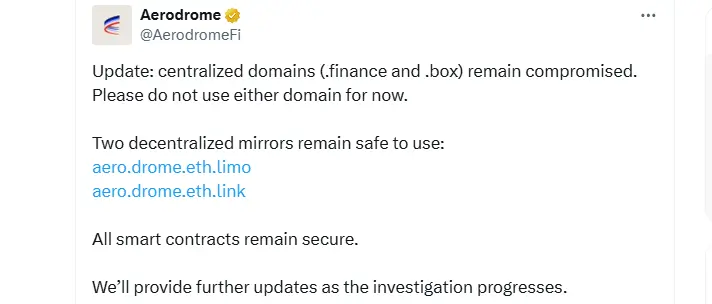
Aerodrome Finance, the largest decentralized exchange on the Base network, issued an urgent alert after discovering that attackers had compromised the project’s primary domains. The team confirmed that its .finance and .box addresses were hijacked, exposing users to fraudulent transaction prompts designed to drain digital assets. While the frontend was affected, the protocol noted that its smart contracts remain intact.
Compromised Domains Trigger Emergency Warnings
According to the project, the breach originated within the DNS layer, affecting the centralized domains managed through Box Domains. Activity linked to the compromise surfaced roughly six hours before Aerodrome released its public warning.
The team initially directed users to two decentralized ENS mirrors, aero.drome.eth.limo and aero.drome.eth.link, which operate outside traditional DNS systems. Soon after, the warning was expanded, advising users to avoid all URLs until the full investigation is completed.
Aerodrome Finance Warns Users After Major Frontend Breach (Source: X)
Velodrome Finance, a related protocol, issued similar statements around the same time, suggesting that multiple platforms relying on the same DNS provider may have been targeted. Both teams stressed that contract-level security was never at risk.
Users Describe Rapid Drain Attempts and Deceptive Approvals
Community reports surfaced as soon as the fraudulent interface went live. One user detailed how the hijacked site first issued a simple signature request containing only the number “1.” After that, the interface pushed a rapid series of unlimited approval prompts covering ETH, NFTs, USDC, and WETH.
The approval spam was structured to drain assets almost instantly if a user signed without noticing the changes in transaction type. Screenshots and video recordings shared online show the sequence in real time.
Early community estimates suggest that more than $1 million was drained across affected Aerodrome and Velodrome users within an hour. One developer shared that they had recently fallen victim to a separate draining incident, despite years of technical experience, and spent three days developing a recovery script to retrieve a portion of their funds.
Investigators reviewing browser setups, extensions, and RPC configurations concluded that the attack aligned with DNS hijacking behavior, not a flaw within Aerodrome’s contracts.
Co-Founder Criticizes Mockery Amid Ongoing Investigation
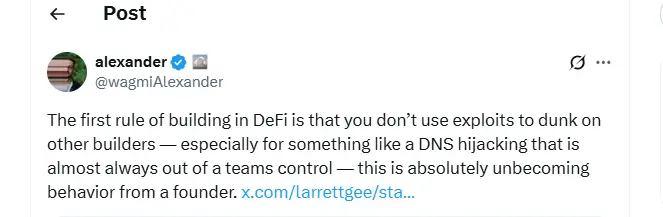
During the response, Aerodrome co-founder Alexander Cutler addressed comments from another builder who mocked the project as the breach unfolded. Cutler stressed that ENS-based domains remained unaffected, 3DNS infrastructure was protected by multisig controls, and several top security teams were involved in the investigation.
Aerodrome co-founder Alexander Cutler addresses the Attack Comments (Source: X)
He added that DNS hijacking incidents rarely stem from errors within a project’s internal systems and cautioned against using attacks as opportunities to criticize other teams.
Incident Follows a Sharp Drop in Monthly Crypto Hack Losses
The Aerodrome breach comes shortly after October recorded the lowest monthly crypto hack losses of the year. Security data shows that only $18.18 million was stolen across 15 incidents, marking an 85.7% decline from September’s $127.06 million.
Excluding the Garden Finance exploit, losses would have settled near $7.18 million, the lowest figure since early 2023. Despite this dip, attackers have grown significantly faster in 2025. A Global Ledger report found that more than $3 billion had already been stolen in the first months of the year.
In many cases, funds were moved or laundered within minutes of an attack. Centralized exchanges processed about 15% of these amounts and remain responsible for more than half of all losses recorded this year. Aerodrome continues to investigate the breach and has urged users to avoid all domains associated with the protocol until the team confirms that access routes are fully secure.